Not it's not my imagination: Spam is on the rise and criminals are to blame. Brings new irony to the phrase "there ought to be a law against it" and deeper for Bill Gates promise that spam will be solved in 2006.
p.s. Wonder why it's spam and not SPAM but sometimes Spam? Get the official word here.
Cybersecurity, AI, crime, fraud, risk, trust, privacy, gender, equity, public-interest technology
Sunday, December 31, 2006
Wednesday, December 27, 2006
Whole New Security Vista? There's a target painted on new Microsoft OS
"Hi-tech criminals are looking forward to the consumer release of Windows Vista, say security experts." BBC News. Why? Because it is presents new opportunities, new possibilities for abuse.
"What?" you say, "surely this is the 'most secure version of Windows yet.'" (As proclaimed by Microsoft.) According to the BBC article, if new features won't get you to upgrade to Vista, security enhancements should, according to the co-president of Microsoft's platform, products and services division, Jim Allchin,. Vista will still be worth getting, thanks to its better defenses against phishing attacks, spyware and other malicious code, Allchin told the BBC. "Safety and security is the overriding feature that most people will want to have Windows Vista for."
Unfortunately, lack of historical perspective is widespread in the marketing sector of the IT industry, and too often it spreads to the media that covers IT. Where are the articles that compare and contrast the claims for Vista with those made for Windows NT, which was also claimed to be the most secure version of Windows yet, as was XP Professional? (Notice a pattern here?)
Believe it or not, I have some sympathy for Microsoft at this point because it is faced with a three-pronged dilemma (and we all know those three-prongers can be painful). Here are the three in play at the moment:
At the turn of the year it is always interesting to consider what the future holds. Will Vista be a boon or a boondoggle? Developments on the security will likely be the deciding factor.
"What?" you say, "surely this is the 'most secure version of Windows yet.'" (As proclaimed by Microsoft.) According to the BBC article, if new features won't get you to upgrade to Vista, security enhancements should, according to the co-president of Microsoft's platform, products and services division, Jim Allchin,. Vista will still be worth getting, thanks to its better defenses against phishing attacks, spyware and other malicious code, Allchin told the BBC. "Safety and security is the overriding feature that most people will want to have Windows Vista for."
Unfortunately, lack of historical perspective is widespread in the marketing sector of the IT industry, and too often it spreads to the media that covers IT. Where are the articles that compare and contrast the claims for Vista with those made for Windows NT, which was also claimed to be the most secure version of Windows yet, as was XP Professional? (Notice a pattern here?)
Believe it or not, I have some sympathy for Microsoft at this point because it is faced with a three-pronged dilemma (and we all know those three-prongers can be painful). Here are the three in play at the moment:
- Claiming that something is the "most secure ever" is like painting a target on it. I recall arguing against the launch of a web security certification program back in about 1996 for this very reason. Hackers were big into defacing web pages at the time and locking down a site was pretty difficult with the tools available. So putting a "Certified Secure" sticker on the home page would have been a red rag to a herd of hackers.
- But Microsoft had to claim Vista wasthe most secure ever because there don't seem to be enough other new things in the OS to warrant paying the asking price for the upgrade.
- But Microsoft is a huge company and [IMHO] it is hard for huge companies to achieve excellence in anything, particularly where there are competing goals.
At the turn of the year it is always interesting to consider what the future holds. Will Vista be a boon or a boondoggle? Developments on the security will likely be the deciding factor.
Thursday, December 21, 2006
California Hacking on Such a Winter's Day: USC hacker sentence after UCLA hack
I thought the juxtaposition of these two stories was interesting, on the 12th and 21st of December:
UCLA warns 800,000 people that hacker gained access to their personal information
USC hacker sentenced to 6 months of home detention
Now add this November nugget to the mix:
Rising cost of data security breaches: $182 per record
Now consider this: the June 2005 breach of USC's online student application system compromised 275,000 records and caused the university to shut down the site for 10 days and the perp gets 6 months home detention. But if the cops had found one twentieth of an ounce of crack on the guy he would be going to jail for a minimum of five years. Somehow, something is screwed up here.
.
UCLA warns 800,000 people that hacker gained access to their personal information
USC hacker sentenced to 6 months of home detention
Now add this November nugget to the mix:
Rising cost of data security breaches: $182 per record
Now consider this: the June 2005 breach of USC's online student application system compromised 275,000 records and caused the university to shut down the site for 10 days and the perp gets 6 months home detention. But if the cops had found one twentieth of an ounce of crack on the guy he would be going to jail for a minimum of five years. Somehow, something is screwed up here.
.
Saturday, December 16, 2006
Internet Explorer 7 User Interface Fiasco: Am I nuts or not?
As astute readers will have surmised, I'm in my mid-fifties. At this time in a person's life it's not unusual to wonder, from time to time: Am I going soft in the head? For me, one of those times was my first use of IE7. Here is a little bit of what the program looked like when I installed it. Astute observers will observe there is no menu bar (File-Edit-View -etc.).
 Because web browsing is now the thing I do the most on my computer--actually writing within the web browser as I am right now--I like to place my browser controls in a particular configuration. And I like some sort of consistency. So I set to work on IE7. I found you can get the old menu bar to show up, but the process is a pain. Furthermore, any further configuration hits the wall pretty quick. For example, the IE7 toolbars won't move, for me. This was so unexpected that I thought for sure my senile dementia was setting in. There I was, clicking and dragging and nothing was happening. In fact, the default UI is such a big departure from a. the norm, b. common sense, I deduced that, because I couldn't 'fix' it, I must be losing my marbles.
Because web browsing is now the thing I do the most on my computer--actually writing within the web browser as I am right now--I like to place my browser controls in a particular configuration. And I like some sort of consistency. So I set to work on IE7. I found you can get the old menu bar to show up, but the process is a pain. Furthermore, any further configuration hits the wall pretty quick. For example, the IE7 toolbars won't move, for me. This was so unexpected that I thought for sure my senile dementia was setting in. There I was, clicking and dragging and nothing was happening. In fact, the default UI is such a big departure from a. the norm, b. common sense, I deduced that, because I couldn't 'fix' it, I must be losing my marbles.
But no! It is Redmond that has lost its marbles on this one. How do I know? Another blog came to my rescue. I found this "Blog of Fusion" and began reading. Phew! It wasn't just me. Others were having the same "issues."
What had me really scared--before I found that blog--was an illustration in an article at microsoft.com. See that "Classic Menu" option? I couldn't find that in my copy of IE7, as shown below. Then I noticed the article was published in June. I had installed the 'shipping' version of IE7 in December. Tthis seems to be evidence that Microsoft--at one point in the Beta--allowed what the shipping version does not allow.
Check out the screen shots. My version of IE7 doesn't allow me to drag toolbars like the article shows. Seems they must have ditched this stuff during the final build and, with breezy indifference, failed to correct their own web site. BTW, that page at microsoft.com is the top result if you Google: internet explorer 7 toolbar customize.
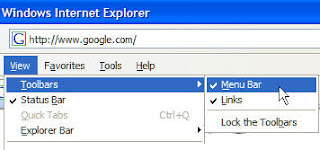 So, can you imagine how many thousands of people around the planet are going to a. try to customize the IE7 toolbar, b. get stuck, c. Google to that page, d. waste hours resolving the resulting contradictions?
So, can you imagine how many thousands of people around the planet are going to a. try to customize the IE7 toolbar, b. get stuck, c. Google to that page, d. waste hours resolving the resulting contradictions?
I mean no offense to the poor microserf who wrote that stuff--he probably asked them to take it down and they didn't. When I was a Microsoft Vendor, everyone that I met in Redmond seemed smart, pleasant, and very earnest, but also out of touch with reality. And the entities to which they reported within the organization were more than a little messed up. In short, a classic example of how a bunch of smart, well-intentioned people can add up to a dumb bunch of decisions. (We are seeing another of these dumb decisions play out right now: "Improved security is the rasion d'etre for the next expensive Windows upgrade.)
One specific criticism of IE7 that I haven't seen elsewhere is that the row for the tabs of the new tabbed browsing feature (a feature that got me using Firefox as my main browser several years ago) seem to be fixed on the same line as the main buttons. This gives decidedly less space to the tabs than you have in Firefox. Also, if you remove the traditional menu, the View command is gone. There is no button for it. So the only way to get the traditional View menu item back is a right click in a select area of the tab/button bar.
Makes no sense to me, and thanks to fellow bloggers, I'm pretty sure I'm not senile, yet.
.
 Because web browsing is now the thing I do the most on my computer--actually writing within the web browser as I am right now--I like to place my browser controls in a particular configuration. And I like some sort of consistency. So I set to work on IE7. I found you can get the old menu bar to show up, but the process is a pain. Furthermore, any further configuration hits the wall pretty quick. For example, the IE7 toolbars won't move, for me. This was so unexpected that I thought for sure my senile dementia was setting in. There I was, clicking and dragging and nothing was happening. In fact, the default UI is such a big departure from a. the norm, b. common sense, I deduced that, because I couldn't 'fix' it, I must be losing my marbles.
Because web browsing is now the thing I do the most on my computer--actually writing within the web browser as I am right now--I like to place my browser controls in a particular configuration. And I like some sort of consistency. So I set to work on IE7. I found you can get the old menu bar to show up, but the process is a pain. Furthermore, any further configuration hits the wall pretty quick. For example, the IE7 toolbars won't move, for me. This was so unexpected that I thought for sure my senile dementia was setting in. There I was, clicking and dragging and nothing was happening. In fact, the default UI is such a big departure from a. the norm, b. common sense, I deduced that, because I couldn't 'fix' it, I must be losing my marbles.But no! It is Redmond that has lost its marbles on this one. How do I know? Another blog came to my rescue. I found this "Blog of Fusion" and began reading. Phew! It wasn't just me. Others were having the same "issues."
What had me really scared--before I found that blog--was an illustration in an article at microsoft.com. See that "Classic Menu" option? I couldn't find that in my copy of IE7, as shown below. Then I noticed the article was published in June. I had installed the 'shipping' version of IE7 in December. Tthis seems to be evidence that Microsoft--at one point in the Beta--allowed what the shipping version does not allow.
Check out the screen shots. My version of IE7 doesn't allow me to drag toolbars like the article shows. Seems they must have ditched this stuff during the final build and, with breezy indifference, failed to correct their own web site. BTW, that page at microsoft.com is the top result if you Google: internet explorer 7 toolbar customize.
 So, can you imagine how many thousands of people around the planet are going to a. try to customize the IE7 toolbar, b. get stuck, c. Google to that page, d. waste hours resolving the resulting contradictions?
So, can you imagine how many thousands of people around the planet are going to a. try to customize the IE7 toolbar, b. get stuck, c. Google to that page, d. waste hours resolving the resulting contradictions?I mean no offense to the poor microserf who wrote that stuff--he probably asked them to take it down and they didn't. When I was a Microsoft Vendor, everyone that I met in Redmond seemed smart, pleasant, and very earnest, but also out of touch with reality. And the entities to which they reported within the organization were more than a little messed up. In short, a classic example of how a bunch of smart, well-intentioned people can add up to a dumb bunch of decisions. (We are seeing another of these dumb decisions play out right now: "Improved security is the rasion d'etre for the next expensive Windows upgrade.)
One specific criticism of IE7 that I haven't seen elsewhere is that the row for the tabs of the new tabbed browsing feature (a feature that got me using Firefox as my main browser several years ago) seem to be fixed on the same line as the main buttons. This gives decidedly less space to the tabs than you have in Firefox. Also, if you remove the traditional menu, the View command is gone. There is no button for it. So the only way to get the traditional View menu item back is a right click in a select area of the tab/button bar.
Makes no sense to me, and thanks to fellow bloggers, I'm pretty sure I'm not senile, yet.
.
Wednesday, December 13, 2006
Need Help With Computer Security? Check cobb.com
Just a quick reminder that you can find a bunch of free articles about computer security at the cobb.com web site. Enjoy!
Note This Blog: Dare Not Walk Alone is now with THINKFilm
 The civil rights film that I have been involved with for the past few years, Dare Not Walk Alone, is making progress!
The civil rights film that I have been involved with for the past few years, Dare Not Walk Alone, is making progress!A major update on the film and related projects, like the campaign to rebuild the house at 521 North Woodlawn that was featured in the film, has just been posted on the Dare Not Walk Alone blog. Check it out!
Monday, December 11, 2006
Blogs of Note: I guess scobb's non-blog made it
 Apparently there is something called "Blogs of Note" and this blog was listed there today. Not sure how much of an achievement that is, but thanks to anyone who might be responsible. I write mainly for my own sanity, but it's encouraging to think some people are reading what I write. To that end may I shamelessly plug some of the other blogs I have been building. They are not all in full flow yet, but getting there.
Apparently there is something called "Blogs of Note" and this blog was listed there today. Not sure how much of an achievement that is, but thanks to anyone who might be responsible. I write mainly for my own sanity, but it's encouraging to think some people are reading what I write. To that end may I shamelessly plug some of the other blogs I have been building. They are not all in full flow yet, but getting there.Obviously, the idea is to group my posts around subject matter. Hopefully it is not too ambitious. Time will tell. I think scobb's non-blog will continue to be the place that I put my thoughts on security.
More Secure Windows May Not Help: BusinessWeek makes a very good point
There's a nice article in Business Week that meshes with my view of computer security. Let me spell this out.
This may sound like a tall order--and it is--the task is not insurmountable. Law and order can eventually replace lawlessness, e.g. the Wild West. Standards of behavior within any given geographic entity can be improved, e.g. reduced drinking and driving in UK/US/et al.
Of course, these are changes that take decades to bring about. All the more reason to commit to the process now, rather than later. Remember, technology cannot create security; the sooner people set aside dreams of security based on the false promise that it can, the sooner the root problem will be addressed, and the better the interim security strategy will be.
- Microsoft is spending a lot of money right now to encourage people who use Windows to upgrade, for a fee, to a new version called Vista.
- To justify the fee for the new version Microsoft is talking a lot about how much more secure Vista is than previous versions of Windows.
- All this talk may be creating an expectation that computer users will encounter fewer security problems in the future.
- This expectation is probably false.
This may sound like a tall order--and it is--the task is not insurmountable. Law and order can eventually replace lawlessness, e.g. the Wild West. Standards of behavior within any given geographic entity can be improved, e.g. reduced drinking and driving in UK/US/et al.
Of course, these are changes that take decades to bring about. All the more reason to commit to the process now, rather than later. Remember, technology cannot create security; the sooner people set aside dreams of security based on the false promise that it can, the sooner the root problem will be addressed, and the better the interim security strategy will be.
Wednesday, November 29, 2006
What Are Security Breaches: Trousers they are not
Are you new to the world of computer security? If so you might appreciate a little orientation lesson.
Failure to prevent the breach may cost the bank money. The bank might be sued by the account holder. The bank may have to divert staff from normal duties to a review of records to determine the extent of the breach. If the breach exposes confidential information about a lot of customers the bank might lose some existing customers who are angry about this, and the marketing dollars that the bank spends to attract new customers might not work for a while due to bad publicity.
In my previous posting I cited a study that put a dollar amount "per record" on the cost of security breaches. I think the number is higher than many businesses realize.
- Computer security is about protecting information that is processed by computers, otherwise known as data, and the processes that use such data. This includes, for example, information about your bank account and how much money you have in it [data] and your ability to withdraw that money [process]. You want the data to be both secret and correct; and you want the process to work on demand. These are the three main pillars of computer security: confidentiality [secret]; integrity [correct]; availability [on demand].
- Computer security can also be referred to as information system security although technically an information system might include other elements besides just computers.
- Information system security is a part, or subset, of information security [because information security includes stuff that is not on computer, like a set of design drawings or company secrets whispered from one person to another].
- Information security can also be referred to as information assurance.
Failure to prevent the breach may cost the bank money. The bank might be sued by the account holder. The bank may have to divert staff from normal duties to a review of records to determine the extent of the breach. If the breach exposes confidential information about a lot of customers the bank might lose some existing customers who are angry about this, and the marketing dollars that the bank spends to attract new customers might not work for a while due to bad publicity.
In my previous posting I cited a study that put a dollar amount "per record" on the cost of security breaches. I think the number is higher than many businesses realize.
Wednesday, November 15, 2006
Rising Cost of Data Breaches: $182 per lost customer record
My hat is off to Larry for his study of security costs. In some ways this latest Ponemon Insitute study is probably more indicative of the state of things than the annual CSI/FBI survey.
If you are trying to get your company to do a better job of securing data, try multiplying the number of customer records your company processes/stores (CRP) times cost of loss per record (CLR) and you might have a good starting point for budgeting project to overhaul your current security (CRP x CLR = the hit to profits from any single incident in which CRP number of records are exposed).
Larry figures the figure for CLR is $182. A breach exposing 10,000 records is thus a $1.82 million problem. Spend that amount on security upgrades and you arguably save an unknown number of exposures (there is nothing that says you won't get hit twice in one year for example). Spend anything less than that and you are playing a high stakes game of chance with your business and, if you are a C-level exec or board member, with your personal and professional liability.
And don't let your managers fob you off with "these studies are just scare tactics." Tell them I know Larry Ponemon and Larry Ponemon is no scaremonger.
If you are trying to get your company to do a better job of securing data, try multiplying the number of customer records your company processes/stores (CRP) times cost of loss per record (CLR) and you might have a good starting point for budgeting project to overhaul your current security (CRP x CLR = the hit to profits from any single incident in which CRP number of records are exposed).
Larry figures the figure for CLR is $182. A breach exposing 10,000 records is thus a $1.82 million problem. Spend that amount on security upgrades and you arguably save an unknown number of exposures (there is nothing that says you won't get hit twice in one year for example). Spend anything less than that and you are playing a high stakes game of chance with your business and, if you are a C-level exec or board member, with your personal and professional liability.
And don't let your managers fob you off with "these studies are just scare tactics." Tell them I know Larry Ponemon and Larry Ponemon is no scaremonger.
Friday, November 10, 2006
Trust in Electronic Voting Eroding Faster Than Florida's Beaches
Yes folks, once again Florida leads the nation in eroding public trust in electronic voting systems. Check out the story so far in Sarasota. Lots of familiar themes and players. Zero doubt in my mind that the books were cooked (based on 30 years of experience with fraud, audit, and computer security).
In keeping with what I have blogged elsewhere, I predict the public will never trust electronic voting as much as paper and pencil ballots. And rightly so. I've worked with computers in all manner of situatons, from auditing oil companies with mainframes to building mission critical networks and securing mobile devices. They work quite well for a lot of things but not everything. I just don't see how you can make a trustworthy voting system out of them. So why bother? What is there to be gained?
In keeping with what I have blogged elsewhere, I predict the public will never trust electronic voting as much as paper and pencil ballots. And rightly so. I've worked with computers in all manner of situatons, from auditing oil companies with mainframes to building mission critical networks and securing mobile devices. They work quite well for a lot of things but not everything. I just don't see how you can make a trustworthy voting system out of them. So why bother? What is there to be gained?
Monday, November 06, 2006
Save Millions on IT: Delay Vista Upgrade
Come on IT people, this is a no-brainer. Don't upgrade to Vista, yet if ever. At least wait until Service Pack 1 has been released and tested (which I predict will be late 2007, early 2008). Here's five ways you save:
About the only redeeming qualities Microsoft can rightfully claim right now is the relative stability of XP and the massive philanthropy of its founder.
Stephen
- Fewer install hassles--let others learn the hard way and smooth it out for you.
- Lower software costs--avoid premiums [and headaches] on new versions.
- Reduced learning curve--if your users get Vista on their home PCs in the first half of 2007 they'll be training themselves.
- Reduced learning costs--as Vista training becomes commoditized.
- Hardware savings--the Vista delay (>2 years) has created a huge hardware surplus.
- Cut analyst bills--don't pay a dime to anyone who told you Vista was on track and early adoption was a good thing.
- shipped far too late but much too soon,
- more trouble than it's worth,
- often followed by successive versions which actually deliver on the original promises.
About the only redeeming qualities Microsoft can rightfully claim right now is the relative stability of XP and the massive philanthropy of its founder.
Stephen
Thursday, September 14, 2006
Wired on Top of Splogs
Correct me if I'm wrong, but Wired seems to be leading the discussion of splogs, those sick abuses of blogging that merely serve to line some sad maladjusted scammer's pockets.
Spam + Blogs = Trouble by Charles C. Mann
How to Fight Those Surging Splogs by Nicole Lee
Proof of another scobb rule: People Will Mess Up Every New Technology for Profit. Of course, there will be counter-attacks as legitimate interests fight back. But don't you just wish humans as a whole were less greedy and just generally better behaved?
Spam + Blogs = Trouble by Charles C. Mann
How to Fight Those Surging Splogs by Nicole Lee
Proof of another scobb rule: People Will Mess Up Every New Technology for Profit. Of course, there will be counter-attacks as legitimate interests fight back. But don't you just wish humans as a whole were less greedy and just generally better behaved?
Thursday, September 07, 2006
Risk displacement and hardware viruses
Check out this timely column from Adrian Kingsley-Hughes:
As Windows becomes harder to crack, could virus writers start to target hardware? "On August 25th, security firm Symantec engineers announced they had discovered a virus that leveraged a flaw in the AMD64 CPU. This virus, called W32/W64.Bounds, was capable of binding itself to Windows executables in such a way that made it hard to detect. However, it's now been shown that this virus doesn't have anything to do with in AMD CPUs, but instead with the X86-64 instruction set itself. But could this be a sign of things to come?"
Anyone who has heard me talk about risk displacement will know my answer to his question: Yes.
As you harden security in one area, softer areas will be targeted. Savvy security managers at large companies learned this in the nineties. As they began to install firewalls most attackers moved on to target other, less protected networks. In fact, this phenomenon is at the heart of the Turntide anti-spam technology that I helped develop. We bet that spam software would not waste bandwidth trying to stuff spam into networks that appear incapable of accepting spam at a high rate of messages per second. We were right.
And as Adrian points out in his column, widely deployed hardware is an attractive target for malware authors. The first Microsoft Word virus did not show up until Word was the most widely used word processing application. Email viruses did not appear until email was widely used. So the big variable in the emergence of a hardware virus threat is the extent to which a "hard to crack" version of Windows is deployed.
BTW, Adrian's web site is a gold mine of useful information about PC hardware and software, check it out at http://www.pcdoctor-guide.com/wordpress/.
As Windows becomes harder to crack, could virus writers start to target hardware? "On August 25th, security firm Symantec engineers announced they had discovered a virus that leveraged a flaw in the AMD64 CPU. This virus, called W32/W64.Bounds, was capable of binding itself to Windows executables in such a way that made it hard to detect. However, it's now been shown that this virus doesn't have anything to do with in AMD CPUs, but instead with the X86-64 instruction set itself. But could this be a sign of things to come?"
Anyone who has heard me talk about risk displacement will know my answer to his question: Yes.
As you harden security in one area, softer areas will be targeted. Savvy security managers at large companies learned this in the nineties. As they began to install firewalls most attackers moved on to target other, less protected networks. In fact, this phenomenon is at the heart of the Turntide anti-spam technology that I helped develop. We bet that spam software would not waste bandwidth trying to stuff spam into networks that appear incapable of accepting spam at a high rate of messages per second. We were right.
And as Adrian points out in his column, widely deployed hardware is an attractive target for malware authors. The first Microsoft Word virus did not show up until Word was the most widely used word processing application. Email viruses did not appear until email was widely used. So the big variable in the emergence of a hardware virus threat is the extent to which a "hard to crack" version of Windows is deployed.
BTW, Adrian's web site is a gold mine of useful information about PC hardware and software, check it out at http://www.pcdoctor-guide.com/wordpress/.
Wednesday, August 30, 2006
No, I won't live and breathe your product!
Why do software makers think you want to live and breathe their product? More and more applications seem to think they are the only reason you bought your computer. Even drivers are getting this way. I have recently installed HP printer drivers that are more than 50 megabytes. They add photoviewing, image management, file transfer, camera interfacing stuff that I don't want. They take over file associations. I bought the printer to print. Period. Am I the only person who just wants an HP printer to print? Or have I missed some liefstyle trend where printers are all about how I see the world and relate to it, digitally speaking?
Apaprently I am not the only person who has gotten ticked off...check out Simon Wilson's rant about the 170 megabyte HP driver. That was a while ago...it would be interesting to know if HP as reacted. It would sure be nice to have the option to go "basic driver only" during the install.
Apaprently I am not the only person who has gotten ticked off...check out Simon Wilson's rant about the 170 megabyte HP driver. That was a while ago...it would be interesting to know if HP as reacted. It would sure be nice to have the option to go "basic driver only" during the install.
Sunday, July 16, 2006
New Microsoft Same as the Old Microsoft?
So Microsoft has spent years perfecting a means of patching holes in its flagship product--the Windows XP operating system--holes that had left XP-based computer systems vulnerable to various types of attack. When your computer is attacked you worry about a number of things, probably three. You don't want strangers accessing your private data (confidentiality). You don't want to your documents messed up (integrity). And you don't want to be denied access to your documents or your system (availability).
Well it seems some recent XP patches are themselves attacking data integrity. I noticed this myself when I came downstairs one recent morning and found my laptop had rebooted itself. The cause of the reboot? The Windows Automatic Update. The effect? A bunch of typing and research was 'lost.' That's right, Windows had rebooted without saving the latest version of my documents (and Microsoft Word did not even offer to recover the work when I re-started it).
I couldn't quite believe this, until I found other people had noticed the same thing. Blogger Tim Rains has a nice piece on this problem and what to do about it.
Well it seems some recent XP patches are themselves attacking data integrity. I noticed this myself when I came downstairs one recent morning and found my laptop had rebooted itself. The cause of the reboot? The Windows Automatic Update. The effect? A bunch of typing and research was 'lost.' That's right, Windows had rebooted without saving the latest version of my documents (and Microsoft Word did not even offer to recover the work when I re-started it).
I couldn't quite believe this, until I found other people had noticed the same thing. Blogger Tim Rains has a nice piece on this problem and what to do about it.
Thursday, July 06, 2006
Getting the Hang of This
So, maybe the point of a blog is to publish stuff that others will not. Like stuff that I have written but some editor somewhere decided was not worthy of publication. Here is an example. Hopefully there will time for more.
Stephen
Stephen
Thursday, March 30, 2006
Laptop Thefts, Spam, and More of Same
Sigh...Some computer security vulnerabilities are timeless:
"Fidelity Investments last week disclosed that someone made off with a laptop containing the names, Social Security numbers and other information for 196,000 current and former Hewlett-Packard employees." Sci-Tech Today
The reasons for stealing laptops may change, but laptops used by business people are, by definition, loaded with business information. Now it seems, owing to corporate stupidity, they are also loaded with large amounts of personal information abouts large numbers of persons. The fact that a company like Fidelity had the 401K details of almost 200,000 people sitting on a laptop (instead of on a server in a locked room) is disturbing but sadly not surprising. It is not the first time something like this has happened and we confidently predict it won't be the last. Here's an article on the subject from 2000, ironically published in the HP Chronicle
As for newer vulnerabilities, there is a pretty good blog put out by Sunbelt, a Florida software company. Has some interesting stories about IE, eBay accounts for sale, and bots that might be used for more than spam (which has not gone away the way that Mr. Gates predicted--although this should come as no surprise, given that every major product in the history of Microsoft has been late).
Stephen
"Fidelity Investments last week disclosed that someone made off with a laptop containing the names, Social Security numbers and other information for 196,000 current and former Hewlett-Packard employees." Sci-Tech Today
The reasons for stealing laptops may change, but laptops used by business people are, by definition, loaded with business information. Now it seems, owing to corporate stupidity, they are also loaded with large amounts of personal information abouts large numbers of persons. The fact that a company like Fidelity had the 401K details of almost 200,000 people sitting on a laptop (instead of on a server in a locked room) is disturbing but sadly not surprising. It is not the first time something like this has happened and we confidently predict it won't be the last. Here's an article on the subject from 2000, ironically published in the HP Chronicle
As for newer vulnerabilities, there is a pretty good blog put out by Sunbelt, a Florida software company. Has some interesting stories about IE, eBay accounts for sale, and bots that might be used for more than spam (which has not gone away the way that Mr. Gates predicted--although this should come as no surprise, given that every major product in the history of Microsoft has been late).
Stephen
Thursday, January 26, 2006
Just in Time: Doom & Gloom for Oh Six
Wow, amazing how fast three months can pass. Here we are, late in January of 'oh six,' and I haven't even issued my annual proclamation about the state of the Internet and e-commerce. However, given my last posting, and my annual predictions in prior years, it probably comes as no surprise that I am not optimistic. Indeed, I can't remember the last time I was optimistic about the outlook for the Internet, maybe it was in the mid-to-late nineties, when I seem to recall a brief lull in virus outbreaks, very little spam or spyware, no phishing and no "for-profit" worms.
Alas, things have gone downhill since then. Sure, I use the Internet for a lot of things and find it incredibly useful. But I do so with trepidation, fully armed with paranoia and a variety of defensive mechanisms. My feeling today is that the incredible usefulness of the Internet is still, for a significant slice of the population, outweighed by the risks. My predictions for 2006? More large-scale privacy breaches, more articles about how some folks are turning away from the Internet, and yet more involvement by organized crime in acts of phishing, worming, and Internet fraud.
Oh, and the usual hand-wringing by countless boards and other bodies set up to "do something about this." Remember folks, we are less than four days away from solving spam, as predicted by Mr. Gates.*
Happy New Year!
Stephen
*Note, for all the things he has done wrong, like break the Sherman Antitrust law, and his failures, like not making Ctrl-Tab work the same in all Microsoft Office applications, I still have to confess immense admiration for Mr. Gates's approach to philanthropy. If only more CEOs, such as those in the drug industry and the petroleum industry, would give of their wealth the way that he has, kids today might not find it so hard to be unselfish.
Alas, things have gone downhill since then. Sure, I use the Internet for a lot of things and find it incredibly useful. But I do so with trepidation, fully armed with paranoia and a variety of defensive mechanisms. My feeling today is that the incredible usefulness of the Internet is still, for a significant slice of the population, outweighed by the risks. My predictions for 2006? More large-scale privacy breaches, more articles about how some folks are turning away from the Internet, and yet more involvement by organized crime in acts of phishing, worming, and Internet fraud.
Oh, and the usual hand-wringing by countless boards and other bodies set up to "do something about this." Remember folks, we are less than four days away from solving spam, as predicted by Mr. Gates.*
Happy New Year!
Stephen
*Note, for all the things he has done wrong, like break the Sherman Antitrust law, and his failures, like not making Ctrl-Tab work the same in all Microsoft Office applications, I still have to confess immense admiration for Mr. Gates's approach to philanthropy. If only more CEOs, such as those in the drug industry and the petroleum industry, would give of their wealth the way that he has, kids today might not find it so hard to be unselfish.
Subscribe to:
Comments (Atom)