On this, the 23rd day of Cybersecurity Awareness Month, it's time to acknowledge something this is both sad and true: cybersecurity awareness sometimes means accepting that some of the things that we enjoy a lot may not do us a lot of good. It's a bit like pumpkin spice lattes: I really enjoy drinking them, but doing so is not particularly good for me, and the science strongly suggests that drinking a lot of them is bad for me.
Likewise, I really enjoy sharing information about myself, but I need to do so carefully in order to minimize certain risks. For example, I should probably think twice about sharing on social media the fact that I really like using the Acme Patient Portal App for Android; and maybe think three times if I've also been sharing lots of pictures of our new cat Nadia while using her name as my password on that portal, and all my other accounts.
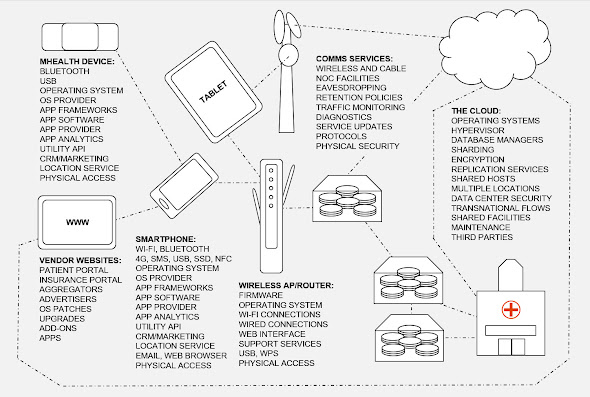
In yesterday's blog post I talked about how serious the threats to health information have become now that so much of it is stored on, processed by, and communicated between, digital devices, things that now range from wearable tracking devices to mainframe computers and huge server farms "in the cloud."
While most people would argue that this massive digitization of medical data is not wrong in itself, criminologists like myself would argue that abuse of this new reality for selfish ends is inevitable, particularly if the data is not protected at all times by "effective guardians" (a term we talked about on Day 7).
Unfortunately, the mass digitization of medical data has been occurring at the same time as an explosion in the number of points at which "bad actors" can attack the systems processing the data, the so-called attack vectors that I referred to on Day 9 (The Internet of Things to Get Smart About). The rapid adoption of everything from tablets to smartphones to connected watches and health trackers is expanding the attack surface, the amount of digital territory that needs to be monitored and defended.
Some years ago I started diagramming this for folks in healthcare, and while it's not the prettiest picture I've ever drawn, I think this one does convey how complex all of these develops have made the task of maintaining cybersecurity:
your doctor; that doctor's colleagues, nurses, and assistants; any specialists you see and staff at the places to which you are referred; your pharmacy; the accounting and administrative departments for all of these; the same again for any insurance companies involved, plus their claims assessors and adjudicators; your employer, who may be paying for all or part of your insurance; and your government, that might be funding, researching, or otherwise tracking some or all of the medical services you need.
#BeCyberSmart


No comments:
Post a Comment